BEC Fraud Revisited
Business Email Compromise (“BEC”) frauds have once again become a major threat for businesses. This method took a backseat to other more sophisticated scams for the last two years, but the scheme has been reinvigorated, once again taking center stage.
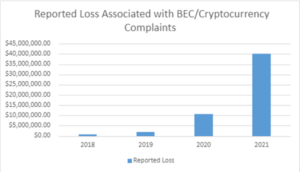
The FBI issued a Public Service Announcement on May 4, 2022[1], in which the Bureau detailed the amount of fraud reported as a result of BEC activities. The amount of fraud is depicted in the following graph:
As is apparent from the graph, the amount of fraud grew significantly over the past year. The COVID-induced remote working environment has only increased the possibility of fraud due to the inability to verify every transaction personally.
Accounts used to perpetrate BEC fraud are generally established in three ways:
The first method hackers deploy is actual access to an email account, where the account is accessed due to a weak password, the use of a compromised password posted on the Dark Web, or a phishing email tricking the user into providing their password. This is the most common method of BEC fraud because it’s efficiency in accessing an account and hijacking a chain of emails.
The second method involves a hacker establishing a look-a-like domain, or a spoofed domain, and creating usernames that appear exactly as the usernames on the company domain. Spoofed domains can be identified through the monitoring of similar domain names.
The third and final method hackers utilize involves the complete compromise of a company’s email server, where hackers remotely monitor communications and even establish a new username on the company’s verified domain. This is the most challenging method, and the least likely to occur, because of the difficulty in hacking the server.
Once an account is established, the fraudster will attempt to search, identify, monitor, and hijack email conversations involving the transfer of money and attempt to convince the sender to transfer money to a bank account controlled by the fraudster. Numerous schemes are deployed by fraudsters but generally involve the following scenarios: a CEO or CFO telling or asking other employees to transfer money, vendors or suppliers asking for payment changes, real estate agents changing closing instructions, and even crypto-currency transfer schemes.
Precautions, which may alleviate the success of such scams, include the following:
- Use multifactor authentication to protect against compromised passwords;
- Regularly updating and patching email servers;
- Establishment of a secondary approval for transactions over certain amounts; and
- Verification of all email addresses before responding to or forwarding a message.
The FBI has a number of other suggestions included on the IC3.gov website.
If you suspect fraud, file a complaint immediately with www.ic3.gov.
Finally, it is vital to note that if frauds caused by BEC are reported immediately, there is a process, referred to as the Financial Fraud Kill Chain (“FFKC”), that may recover lost funds. The FFKC can reverse a fraudulent transfer if the matter is reported immediately. The FFKC has a 72-hour time limit, after which the transaction will no longer be reversible, but before that time has expired, there is a high likelihood that funds can be recovered.
Baird Holm, LLP also maintains a hotline and tools for any assistance with a BEC fraud.