Business Email Compromise and the Financial Fraud Kill Chain
Hackers and scammers have attempted to hijack email accounts and convince unsuspecting victims to transfer money overseas using multiple scam scenarios: lottery scams, the grandparent scams, dating scams, and more. But recently the number of scam emails focusing on hijacking the emails of executives of larger companies has significantly increased. These targeted phishing attacks (i.e., spear phishing or whaling) has a single purpose – to take over the account of an executive and use the email account to convince other employees to transfer company money overseas. The scam is known in federal law enforcement as the CEO scam or more generically as the Business Email Compromise (BEC).
The Federal Bureau of Investigation (FBI) estimates that billions of dollars have been lost to email schemes since the inception of the scam. For example, in 2015 alone, over $263 million based on over 7,800 complaints were reported to the FBI through their internet complaint portal ic3.gov. This information is based on the FBI’s ic3 report on statistics and losses due to cybercrime.
Types of Scams
The BEC scam generally can take several different forms:
The CEO scam
In this form of the BEC scam, the email of the CEO is compromised. The email can either be the personal email or the business email of the CEO, but the scam is most effective if the email which has been compromised is the email account the CEO uses to communicate with the company’s bank or with the company’s financial officer. Thus, a compromised email account can be used to ask a bank or a financial officer to facilitate the transfer of money overseas to an unknown account under the belief that the money is being used to facilitate a business deal. This type of scam is even more effective if it is done while the CEO is traveling and is unavailable via phone to confirm or deny the legitimacy of the transactions.
The Supplier Scam
In this version of the BEC, the email of a vender is compromised. The compromised email account is then used to convince the company that there has been a new bank and new account established to receive transferred funds. The scam is usually discovered only after the legitimate vender complains that payment has not been received which could be several months later depending on the terms of purchase.
The Vendor / Customer Scam
In the final version of the scam, a company’s customer list is compromised and the fraudster uses the address list to request that all future payments be forwarded to a different bank and account. Instead of just targeting one vendor or supplier, this fraud targets all the customers of a company. The fraud is usually not discovered until payment is not received for an item.
Recently, the BEC scam has targeted title companies. Title companies often have one or two large wire transfers to close on a loan. The fraudsters target those transfers and request the closing parties forward their payments to a new bank and account number. The fraud is usually discovered at closing time and can have quite an impact on an individual closing on a home.
Another growing trend is for the fraudsters to target attorney’s offices and attorney’s emails accounts as well. The attorney email may ask for a victim to act quickly for a time-sensitive matter, request the attorney to accept a transfer as part of a settlement, or simply use an attorney to add legitimacy to one or more of the other BEC scams.
Uniform Commercial Code
Article 4A of the Uniform Commercial Code (UCC) sets forth general rules for wire transfers a bank conducts on behalf of its customers. While UCC 4A contains useful provisions allowing a bank to pass liability onto its customer – provided commercially reasonable procedures for initiating a wire transfer are established, agreed to, and utilized – the article is less helpful in helping banks navigate how to address fraudulent transactions, and recoup funds, without having to pass liability onto their own customers. Because of this, it is helpful for banks to have an understanding of how wire transfer fraud takes place, what can be done to prevent it, and what steps the bank may take in the aftermath to recoup funds.
The FBI Response
The losses have generated such a large outcry that the FBI formed a plan based on utilizing the contacts at the Financial Crimes Enforcement Network or FinCEN. FinCEN is the financial crimes intelligence group of the United States. As such, it collects information on scams within the US and shares that information through its networks of financial intelligence groups around the world. To facilitate this information sharing, the intelligence groups of over 140 different countries combined to form the Egmont group. The Egmont group is a world-wide organization of intelligence units to share information on the latest money laundering information and scams and schemes.
As part of the Egmont group, FinCEN is able to request the help and aid of member countries and to seek a return of the money transferred to the country as part of a fraud. TheFBI has maintained a liaison at FinCEN for over 10 years to facilitate the transfer of intelligence between the two organizations. In response to the BEC scams the FBI has begun to use the liaison to assist in the recovery of money lost during a BEC scam. Time is of the essence in the recovery of the money.
Because of the FBI’s relationship with FinCEN, the FBI is in a unique position to attempt to freeze the transfer and in some cases get the money transfer reversed. Since the FFKC was initiated in February of 2016, the FBI reported the following numbers through January of 2017:
- The FFTK Total Request Initiated: $139,984,922
- Total Amount Returned to Victims: $66,802,680
- Total Amount Frozen in Place: $34,512,303
In order to promote this ability the FBI issued an outreach statement outlining the time frame and the type of information needed to recover the money. The information required by the FBI includes:
- Originating Name:
- Originating Location:
- Originating Bank Name:
- Originating Bank Account Number:
- Recipient5 Name:
- Recipient Bank Name:
- Recipient Bank Account Number:
- Recipient Bank Location (if available):
- Intermediary Bank Name (if available):
- SWIFT Number:
- Date of the Transaction:
In addition to the above information, it should be noted that the FBI threshold for attempted retrieval of the money is $50,000.
The above information needs to be reported to the FBI with 72 house of the transfer in order to either freeze or reverse the transfer. After 72 hours the FBI, FinCEN, and the Egmont Group through their related FIUs will be unable to stop the transfer.
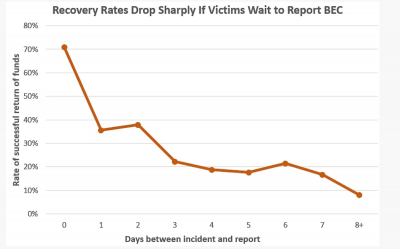
Even if the transfer is past the 72 hours or under the monetary threshold, it is still a good idea to file a complaint with the FBI through ic3.gov. The information provided by you in a scam can be used to possibly identify a subject of another scam, prevent another scam, or even identify an account used by a fraudster. Some of the information collected and tracked by ic3.gov includes:
- IP and/or e-mail address of fraudulent e-mail
- Date and time of incidents
- Incorrectly formatted invoices or letterheads
- Requests for secrecy or immediate action
- Unusual timing, requests, or wording of the fraudulent phone calls or e-mails
- Phone numbers of the fraudulent phone calls
- Description of any phone contact to include frequency and timing of calls
- Foreign accents of the callers
- Poorly worded or grammatically incorrect e-mails
- Reports of any previous e-mail phishing activity
All of this information is useful and relevant if not for your own complaint then for the scams to which others may be a victim.
For further information on the BEC scam, statistical information, and/or to report a fraudulent transfer please visit ic3.gov.


