NIST Standards Are Now Even More Important to HIPAA
Once again, cybersecurity is proving to be a common subject that Congress and the President can agree upon. On January 3, 2021, President Trump signed into law a bill which potentially reduces fines, audits, or mandated remedies for covered entities that have been victims of a breach, however, covered entities must demonstrate an adherence to recognized cybersecurity standards.
H.R. 7898
The new law provides that subtitle D of the Health Information Technology for Economic and Clinical Heath Act (HITECH)[1] is amended to mandate that the Secretary of the Department of Health and Human Services “shall consider whether the covered entity or business associate has adequately demonstrated that it had, for not less than the previous 12 months, recognized security practices in place”. Such a demonstration by the organization may
(1) mitigate fines under section 1176 of the Social Security Act (as amended by section 13410);
(2) result in the early, favorable termination of an audit under section 13411; and
(3) mitigate the remedies that would otherwise be agreed to in any agreement with respect to resolving potential violations of the HIPAA Security rule.
The law defines the term “recognized security practices” as “standards, guidelines, best practices, methodologies, procedures, and processes developed” either by the National Institute for Standards and Technology (“NIST”), developed under section 405(d) of the Cybersecurity Act of 2015, or other cybersecurity “programs and processes which are developed, recognized, or promulgated” under other statutory authority.
NIST Controls
NIST has developed and published a well-known and highly regarded set of cybersecurity standards which are known by their publication number, NIST SP 800-53.[2] The standards are mandatory for government organizations and, often times, by organizations doing business with the government through regulations such as the Federal Information Security Modernization Act (“FISMA”), the Federal Risk and Authorization Management Program (“FedRAMP”), and others. The NIST cybersecurity controls are categorized into 18 different “families” of controls which govern everything from access control and asset protection to secure communications and change management.
The NIST controls have been adopted and used by healthcare organizations as the basis for IT administrative, technical, and physical policies as required by the Health Insurance Portability and Accountability Act of 1996 (“HIPAA”). To aid in use of NIST control statements for HIPAA related IT policies, NIST published a crosswalk between the HIPAA requirements and the NIST framework. NIST SP 800-66 Rev. 1 provides the HIPAA Security Rule Standards, Implementation Specifications, and the relative references to specific NIST control mapping for reference and implementation. There are a number of other organizations and publications which provide similar crosswalks as well. The following is an example of the crosswalk provided by NIST in SP 800-66[3]:
The Cybersecurity Act of 2015
The NIST guidelines first released in 2006 have become synonymous with cybersecurity, but until the Cybersecurity Act of 2015 were not often used in private industry. The reason being that the controls were established to provide a very robust set of controls for government systems using or processing classified, secret, or top-secret information, and if fully implemented were too robust for even large private companies. Private companies began to use parts of the framework, however, as an increasing number of companies were required to do so in order to process or house government data.
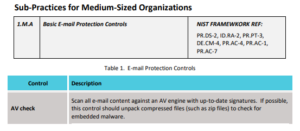
The Cybersecurity Act of 2015 was signed into law by then President Obama and Section 405(d) of that law directed Health and Human Services (“HHS”) to form a Task Group (“CSA-TG”) to develop a common set of voluntary, consensus-based, and industry-led guidelines, practices, methodologies, procedures, and processes that healthcare organizations can use to enhance cybersecurity.”[4] The CSA-TG published two sets of practices: “Technical Volume 1: Cybersecurity Practices for Small Health Care Organizations”, and “Technical Volume 2: Cybersecurity Practices for Medium and Large Health Care Organizations”. Both volumes provide specific standards, steps, controls, and guidelines to create a compressive and scalable set of policies for healthcare organizations as well as direct references to NIST control statements.
A sample of the control from Technical Volume 1[5]:
Practical Application of H.R. 7898
The practical application of the new law is that if an organization can directly tie their policies and procedures to standards promulgated by NIST or by the CSA-TG, then the resulting fines, audits, and mandated mitigation remedies may be reduced in terms of time and money.
Healthcare organizations of all sizes should take the time to create a crosswalk between their policies, policy statements, controls, and procures and NIST, the Task Group, or other statutorily recognized framework. A crosswalk or even a direct reference to such a framework will help healthcare organizations demonstrate their adherence to statutorily recognized frameworks and possibly reduce any fines, terminate an audit, or mitigate any mandated remedies imposed by the Office of Civil Rights.
[1] 41 USC 17931 et seq.
[2] https://csrc.nist.gov/publications/detail/sp/800-53/rev-4/final; the set of standards is currently in its fourth revision and is often cited as NIST 800-53 Rev. 4 as well.
[3] NIST SP 800-66 Rev. 1, page D-17
[4] https://www.phe.gov/Preparedness/planning/405d/Pages/default.aspx
[5] Technical Volume 1: Cybersecurity Practices for Small Health Care Organizations, page 15 (truncated for display)