A Review Of Cyber Breaches In 2019 – Part III
Each year we review the cyber breaches as reported to the Nebraska Attorney General’s Office. This article is the last of three articles to review the reported information. In this final article we look at the types of breaches suffered by businesses and how the breaches occurred.
Types of Breaches Suffered by Companies
Knowing the types of breaches affecting companies helps companies plan and prepare for breach threats. For example, knowing that lost computers cause breaches, companies can draft policies and procedures that require encrypted hard drives or require training for employees taking laptops or USB drives out of the office. Or for example, we see that companies suffer a large number of breaches from phishing schemes, so companies can institute policies that require training on spotting phishing emails and how to report phishing attempts.
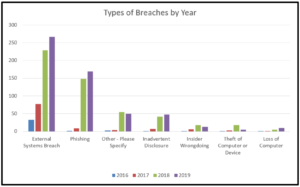
The types of breaches reported by companies to the Nebraska Attorney is represented by the following graphs:
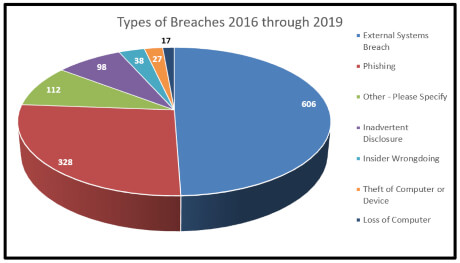
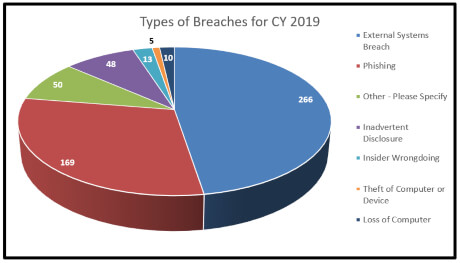
The information reported in 2019 is very similar to the information reported over the entire period of 2016 through 2019. The one noticeable difference is that phishing schemes have become a larger percentage of cases reported.
Vectors of Breaches
The biggest threat to businesses by far is an external system breach. Phishing attacks are the second most common method of attacks leading to breaches suffered by businesses. When the two are combined, they account for close to 75% of all of the breaches perpetrated.
It is important to point out that phishing attacks are both a type of breach and a vector of attack. Many external breaches began as a phishing attack. For example, if a user of an email account suffered a phishing attack and lost control of their credentials, the breach would be an external attack but the means or vector by which the attack was perpetrated was through a phishing attack. According to the data, seven (7) breaches were external system breaches perpetrated via phishing attacks, but many more appear to be related to a phishing attack based on the general description of the attack in the report.
Outside of phishing attacks, some of the external attacks included malware or skimming software installed on an external payment processing system, credential stuffing attacks, malware or ransomware on a company server, physical skimming devices, vendor breaches, or email compromises. The first two types of attacks on external payment processing systems and credential stuffing attacks are addressed in turn below.
Compromise of Payment Processors
Many businesses hire third party processors to process payments and credit card transactions for their online sales. These third party vendors are often the targets of hackers because of the large number of credit cards and financial account numbers processed and financial information they possess. A breach of a company’s third-party processor often leaves the business with the cost of notifying the end user. The processor’s only obligation may be notification to the business of their breach, and the business, in turn, is then responsible to the end user or customers for notification and remediation. Given that a business does not exercise control over the processors systems, businesses may want to consider shifting liability and cost risks before signing a processing contract. For instance, a business can ask the processor to carry insurance and the proceeds can be used to pay notification or cyber response charges.
Credential Stuffing Attacks on the Rise
A credential stuffing attack is one in which an attacker uses an email and a series of well-known or well-researched passwords to attempt to access a password protected site. Recently such attacks have been on the rise because of the large number of usernames and passwords accessible on the web for free. One such list includes 1.4B usernames and passwords. There are several such lists on the Internet which include information from old breaches such as those suffered by LinkedIn, Yahoo, or Marriott. Although these are old passwords, many users never change their old passwords or they may use a series of easily guessed passwords, e.g. “rolltide” and then “RollTide” and finally “RollTide#”. As new passwords are disclosed with new breaches hackers can sometimes guess the next iteration of a password. A good takeaway here is that businesses should ensure employees do not use the same password for work which they use for social networking sites or personal email accounts.
Breaches Over Time
Finally, the types of breaches has changed over time. A look at the graph below indicates that while external threats are on the rise, some internal threats are declining. A company’s quickest and simplest method to deal with cyber threats is through employee education and policy planning and implementation. Internal threats are something a company can control, while external threats are usually outside the control of the company. The reduction in internal employee threats depicted in the graph suggests that companies have and continue to shore up internal threats, reducing their overall cyber-threat exposure.